Wanna Decrypter 2.0 ransomware attack: what you need to know
It was a difficult Friday for many organizations, thanks to the fast-spreading Wanna Decrypter 2.0 ransomware that started its assault against hospitals across the UK before spilling across the globe.
The attack appears to have exploited a Windows vulnerability Microsoft released a patch for in March. That flaw was in the Windows Server Message Block (SMB) service, which Windows computers use to share files and printers across local networks. Microsoft addressed the issue in its MS17-010 bulletin.
SophosLabs said the ransomware – also known as WannaCry, WCry, WanaCrypt and WanaCrypt0r – encrypted victims’ files and changed the extensions to .wnry, .wcry, .wncry and .wncrypt.
Sophos is protecting customers from the threat, which it now detects as Troj/Ransom-EMG, Mal/Wanna-A, Troj/Wanna-C, and Troj/Wanna-D. Sophos Customers using Intercept X will see this ransomware blocked by CryptoGuard. It has also published a Knowledge Base Article (KBA) for customers.
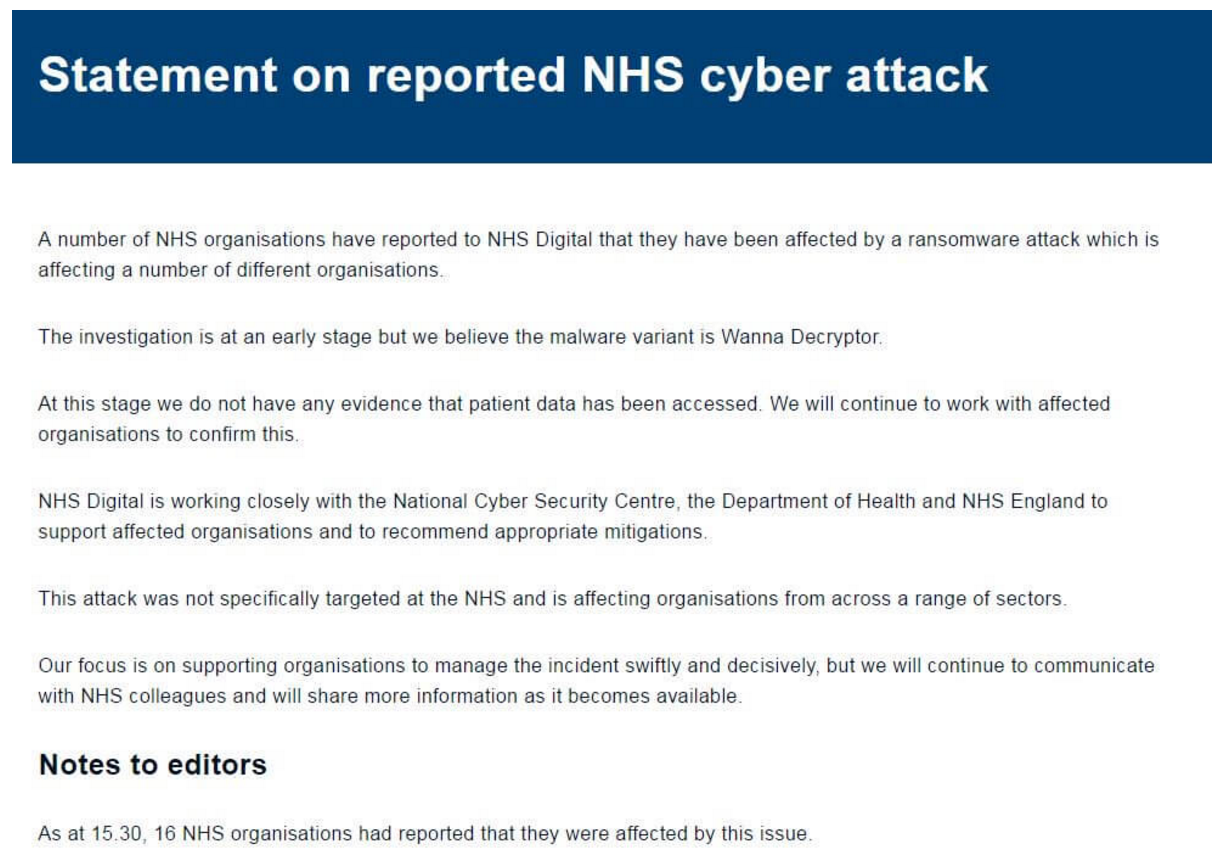
NHS confirms attack
National Health Service hospitals (NHS) in the UK suffered the brunt of the attack early on, with its phone lines and IT systems being held hostage. NHS Digital posted a statement on its website:
The UK’s National Cyber Security Centre, the Department of Health and NHS England worked Friday to support the affected hospitals, and additional IT systems were taken offline to keep the ransomware from spreading further.
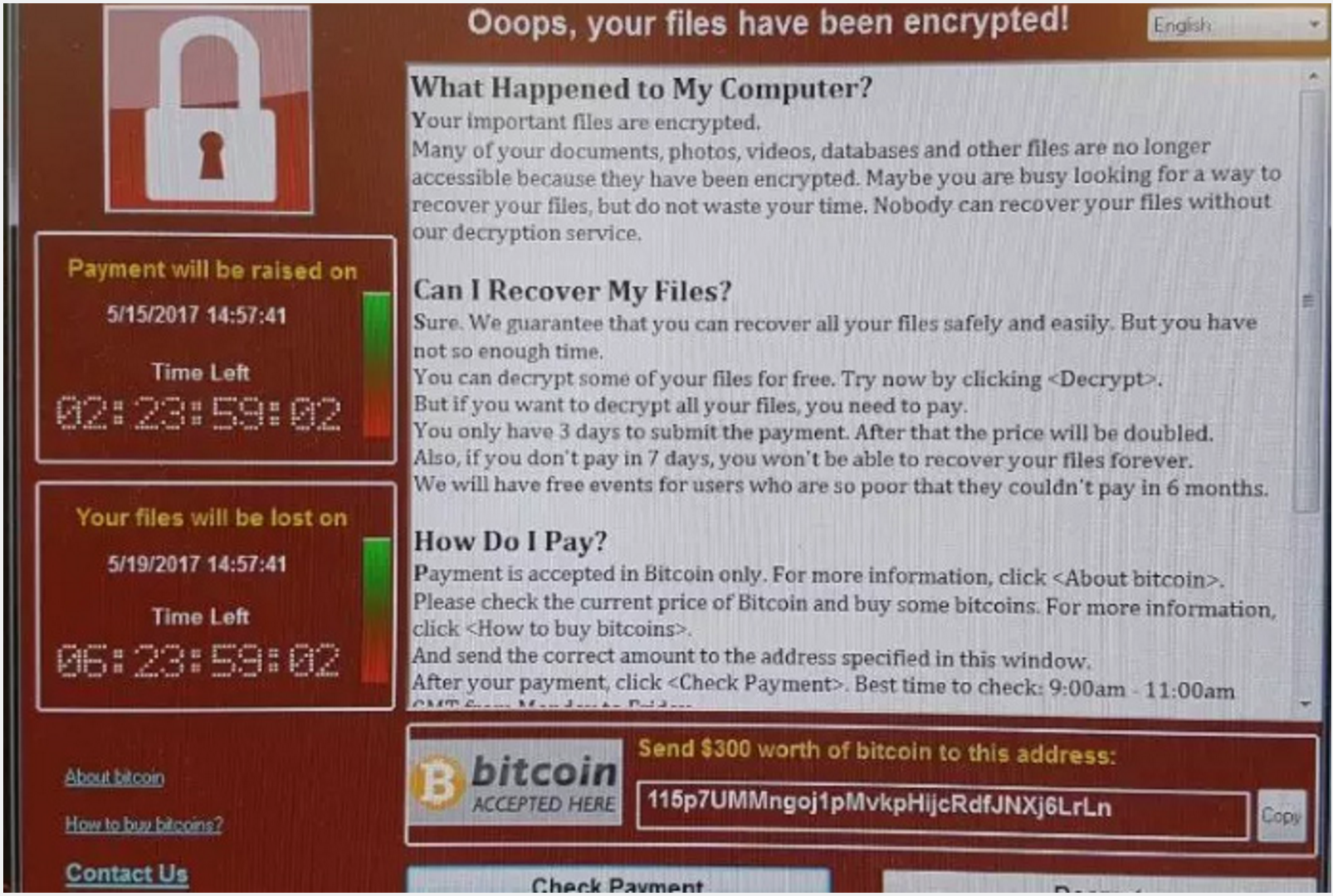
Victims of the attack received the following message:
More guidance from Sophos
As noted above, Sophos has issued protection for customers. But to sum things up:
What to do
Sophos Intercept X customers – no action required
Sophos Endpoint Protection customers – please update your products immediately for protection
Defensive measures
In addition to the guidance above, we urge those who haven’t yet done so to apply Microsoft’s patch. We also recommend companies and individuals:
Resources
Other links we think you’ll find useful:
The attack appears to have exploited a Windows vulnerability Microsoft released a patch for in March. That flaw was in the Windows Server Message Block (SMB) service, which Windows computers use to share files and printers across local networks. Microsoft addressed the issue in its MS17-010 bulletin.
SophosLabs said the ransomware – also known as WannaCry, WCry, WanaCrypt and WanaCrypt0r – encrypted victims’ files and changed the extensions to .wnry, .wcry, .wncry and .wncrypt.
Sophos is protecting customers from the threat, which it now detects as Troj/Ransom-EMG, Mal/Wanna-A, Troj/Wanna-C, and Troj/Wanna-D. Sophos Customers using Intercept X will see this ransomware blocked by CryptoGuard. It has also published a Knowledge Base Article (KBA) for customers.
NHS confirms attack
National Health Service hospitals (NHS) in the UK suffered the brunt of the attack early on, with its phone lines and IT systems being held hostage. NHS Digital posted a statement on its website:
The UK’s National Cyber Security Centre, the Department of Health and NHS England worked Friday to support the affected hospitals, and additional IT systems were taken offline to keep the ransomware from spreading further.
Victims of the attack received the following message:
More guidance from Sophos
As noted above, Sophos has issued protection for customers. But to sum things up:
What to do
Sophos Intercept X customers – no action required
Sophos Endpoint Protection customers – please update your products immediately for protection
Defensive measures
In addition to the guidance above, we urge those who haven’t yet done so to apply Microsoft’s patch. We also recommend companies and individuals:
- Back up regularly and keep a recent backup copy off-site. There are dozens of ways other than ransomware that files can suddenly vanish, such as fire, flood, theft, a dropped laptop or even an accidental delete. Encrypt your backup and you won’t have to worry about the backup device falling into the wrong hands.
- Be cautious about unsolicited attachments. The crooks are relying on the dilemma that you shouldn’t open a document until you are sure it’s one you want, but you can’t tell if it’s one you want until you open it. If in doubt, leave it out.
- Use Sophos Intercept X, which stops ransomware in its tracks by blocking the unauthorized encryption of files.
Resources
Other links we think you’ll find useful:
- To defend against ransomware in general, see our article How to stay protected against ransomware.
- To protect against JavaScript attachments, tell Explorer to open .JS files with Notepad.
- To protect against misleading filenames, tell Explorer to show file extensions.
- To learn more about ransomware, listen to our Techknow podcast.
- To protect your friends and family against ransomware, try our free Sophos Home for Windows and Mac.
via nakedsecurity